Earlier this year, in response to some previous DDoS attacks on a Garry’s Mod server, I developed a fully automated script to detect “anomalies” in traffic, create a tcpdump for later analysis, and block it. I found this attack particularly interesting.
There were 12 desperate attacks that day, trying all different methods. Due to my time, I would like to focus on just one.
Analysis of the attack
Surprisingly, the attack lasted no longer than two minutes with a peak of 325 Mbps incoming traffic to port 27015 (game server).
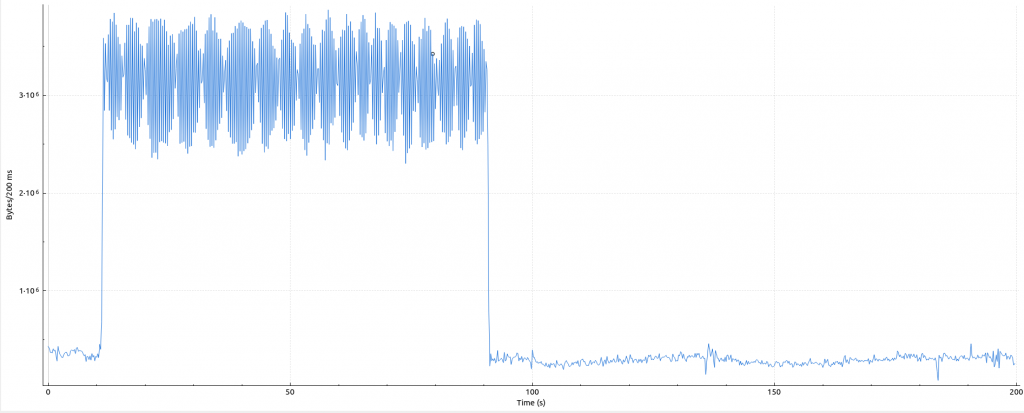
The bandwidth is also in line with Cloudflare’s interesting statistics.
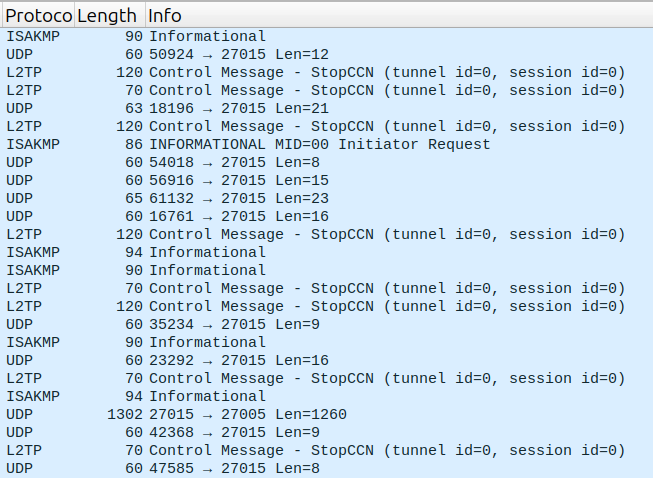
The attack was probably launched by a cheap DDoS booter service and exploited amplification bugs on unpatched devices. Within this timespan a total of over 200.000 hosts were involved using protocols like L2TP, ISAKMP or just raw UDP.
Solution
Defending a game server brings a huge advantage: you know which connections are legitimate.
- Collect a list of IP addresses of all players connected to your server in the last couple of days
- This collection happens inside the game logic and only for fully connected players
- Create a script that reads the rx bytes on your servers interface
- If it reaches a specified threshold load the list of addresses inside an ipset
- Automatically create iptable rules to drop all udp traffic in PREROUTING
- Whitelist udp connections using the created ipset
- Wait until attack is over
- Restore old iptable rules
Limits of this approach are:
- No new players can join in this timespan (which is not that bad compared to the impact of an DDoS attack)
- We are limited to our maximum interface bandwidth of the server
Besides the limits, this is (I hate to do such claims) the best method possible to defend any DDoS attacks if we are limited to a single server. Without this knowledge, it is significantly more difficult and unreliable to block attacks of this magnitude independently and without the help of a third-party vendor.
With each attack, the protection can be improved further and further on the basis of the collected analysis data.

