After I discussed an earlier DDoS attack this year there had been another interesting attack.
However, this time it is such a bad attack that I wonder how an advertised DDoS protection of the hosting provider could not detect this…
If you as a provider fail at such a simple task, either the end user is too dumb to use the product or an attack is considered as legitimate traffic, because you never know what people want to do with their bandwidth…
Analysis of the attack
The attack had the following phases:
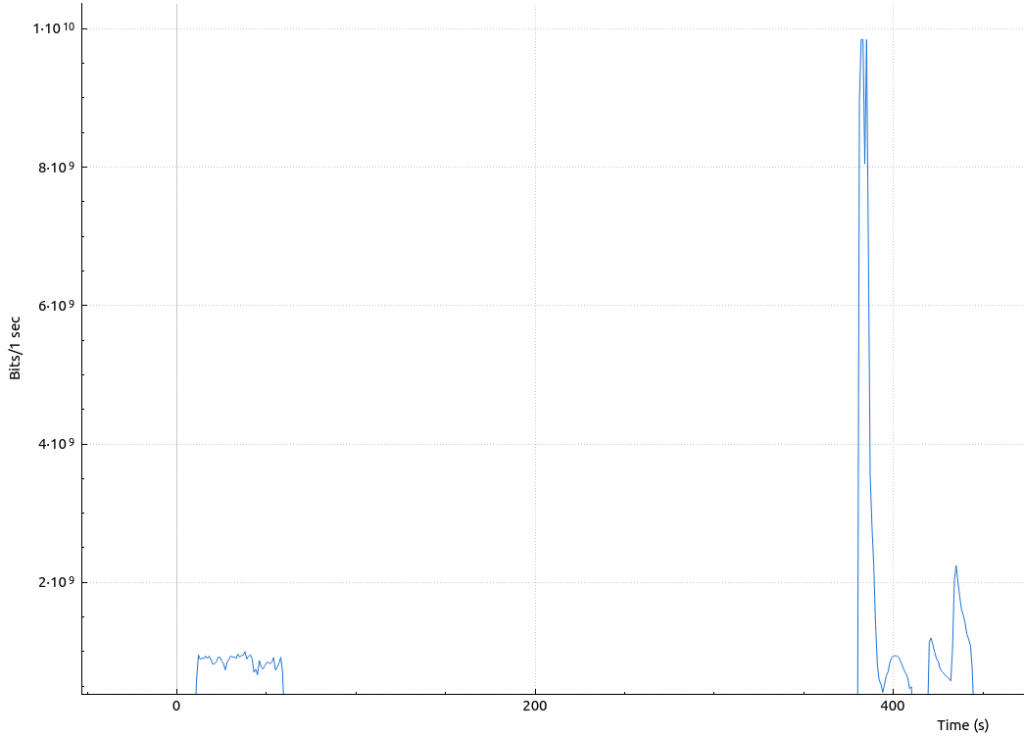
Having a look at the Wireshark graph there had been two attacks:
- 23:40:27 – 23:42:36 (~900 mbps)
- 23:46:38 – 23:55:25 (~9.830 mbps)
The last DDoS attack had over 200.000 distributed hosts attacking the gameserver. This time there had been only 4 hosted on following platforms:
- Google Cloud Platform
- Microsoft Azure
- OVH
Therefore, it can be assumed that the attackers were four powerful VPS or baremetal servers, which often have a high bandwidth.
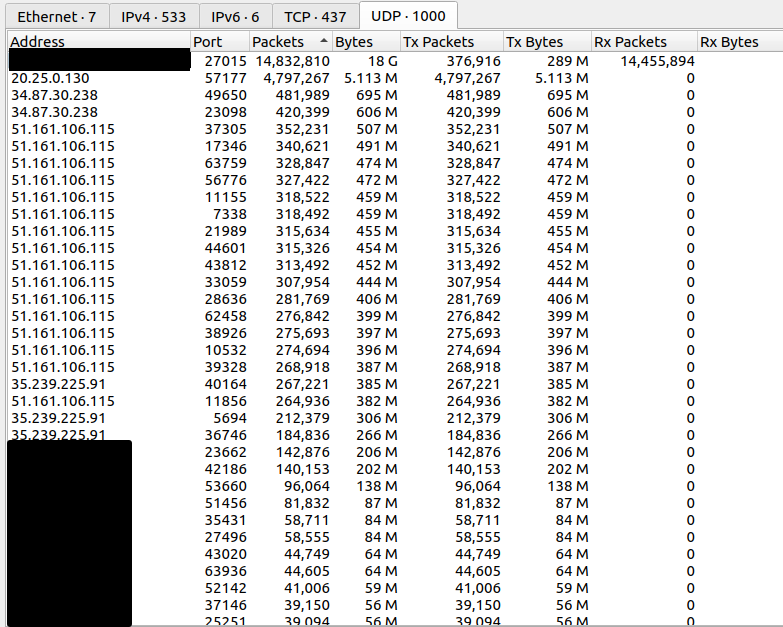
Of course, it would be trivial to simply block the attack manually by blocking the four IP addresses in the provider’s firewall (via the admin interface). So it couldn’t be a serious threat and it was clear that there was no person behind it who had even a little idea of what they were doing.
The funny thing about this attack was the sheer waste of ingenious ways to make a DDoS attack hurt.
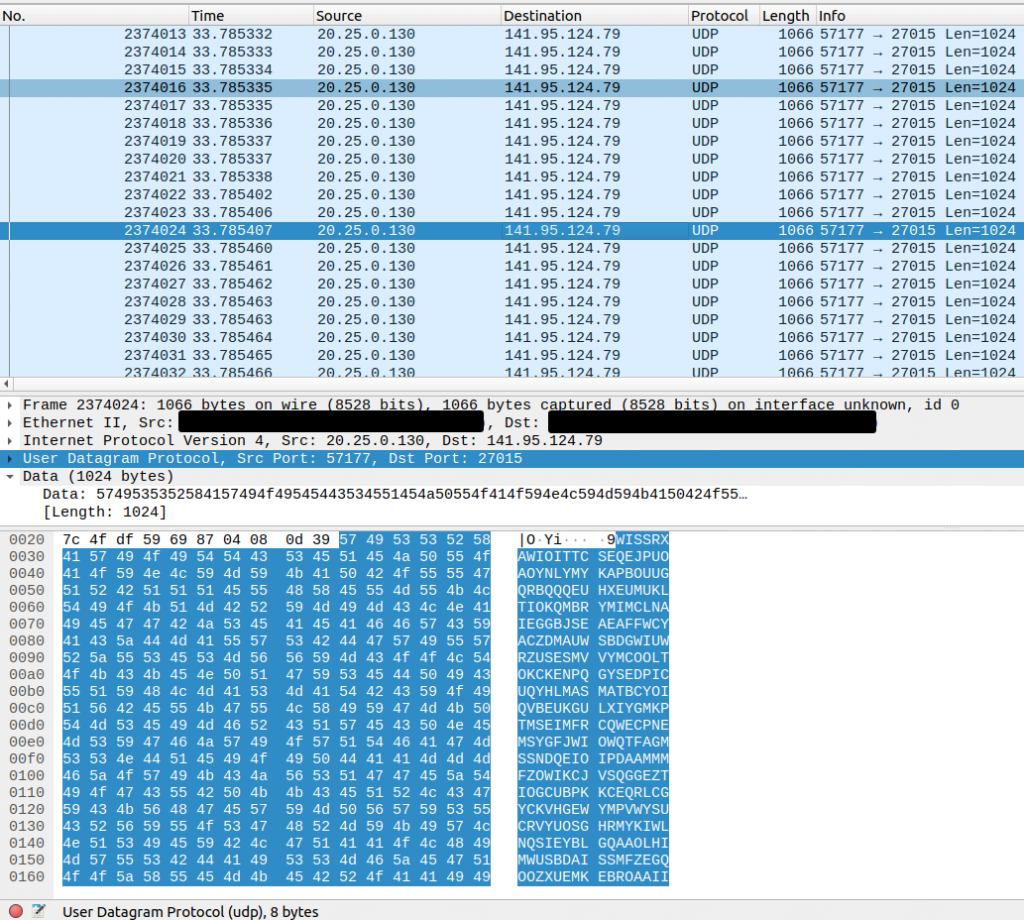
All packets had the identical source port, source port, packet length and packet contents. There was NOTHING randomized at all. A behavior that can be implemented in 10 lines of code.
Solution
The attack was repelled without any problems using the methods mentioned in the past, and there was no sign of any impairment.

