The main goal of digital forensics is the extraction of data from electronic evidence and its subsequent analysis and processing into usable information. A major challenge lies in the flexibilization and modernization of existing forensic tools for the acquisition of evidence. However, most tools are tied to specific hardware, operating systems or architectures, which limits their application possibilities with regard to different use cases and requirements.
Similar to developments in other areas of information technology, a large number of products for securing digital evidence have become established over the past decades. The constant change in technical conditions has had different effects on the development of these products.
Problems
Structural changes to operating systems result in incompatibility with older products whose further development has been discontinued. At the same time, new projects specializing in a specific operating system or individual functionality are emerging due to increasing complexity1.
The spread of proprietary operating systems and specialized hardware poses a significant challenge to the development and maintenance of open source forensics tools. Since the release of Apple’s first Arm-based system-on-a-chip (SoC) for Mac computers in 20202, no open or non-commercial tool exists to secure physical memory. Despite Chromebooks accounting for 15.2 percent of global notebook shipments in 20213, the Scientific Working Group on Digital Evidence (SWGDE) describes best practices for Chromebook acquisition and analysis in the document Best Practices for Chromebook Acquisition and Analysis4:
„Validated tools for the acquisition of Chromebooks are limited. Encrypted user data is stored in the internal memory; however, a large amount of data is stored in the cloud. Without an associated Google account and password for the device, most recoverable user data will be encrypted.“
Although the restriction of access to required interfaces by the mentioned manufacturers serves to protect the privacy and security of users, it represents a considerable obstacle for digital forensics. Conventional software or hardware equipment is often not sufficient to access encrypted or isolated data. The resources and legal capabilities of open source projects are often insufficient to develop specialized tools that can overcome these barriers. Commercial providers, such as Cellebrite5 or products like Magnet Graykey™6, are exclusively accessible to law enforcement agencies and usually use vulnerabilities unknown to the manufacturer that are required to access protected data.
The mentioned challenges promote an increased dependency on cost-intensive, proprietary complete solutions, which makes it more difficult for the open source community to develop competitive alternatives. This leads to users relying on a variety of separate tools instead of having a comprehensive solution. Compared to complete solutions, combining multiple tools is more time-consuming and error-prone.
Approach through automation
The aim of my bachelor thesis was to develop a platform-independent open-source framework that accelerates and simplifies the evidence acquisition process by automating existing forensics tools in a user-defined sequence to suit the identified platform.
How it works
The framework provides a platform as a central entry point, which contains predefined functions and a configuration language for automation. This work does not aim to replace or improve the functionality of already established forensics tools on the market. Instead, it offers the opportunity to integrate and automate products that are already established on the market into the framework.
It is portable and can be executed via USB or a network drive, regardless of the underlying hardware or architecture. It also automatically generates reports with timestamps, checksums and all actions performed to ensure complete reproducibility. Furthermore, it enables users to benefit from individual components without being dependent on the entire functional scope of the framework.
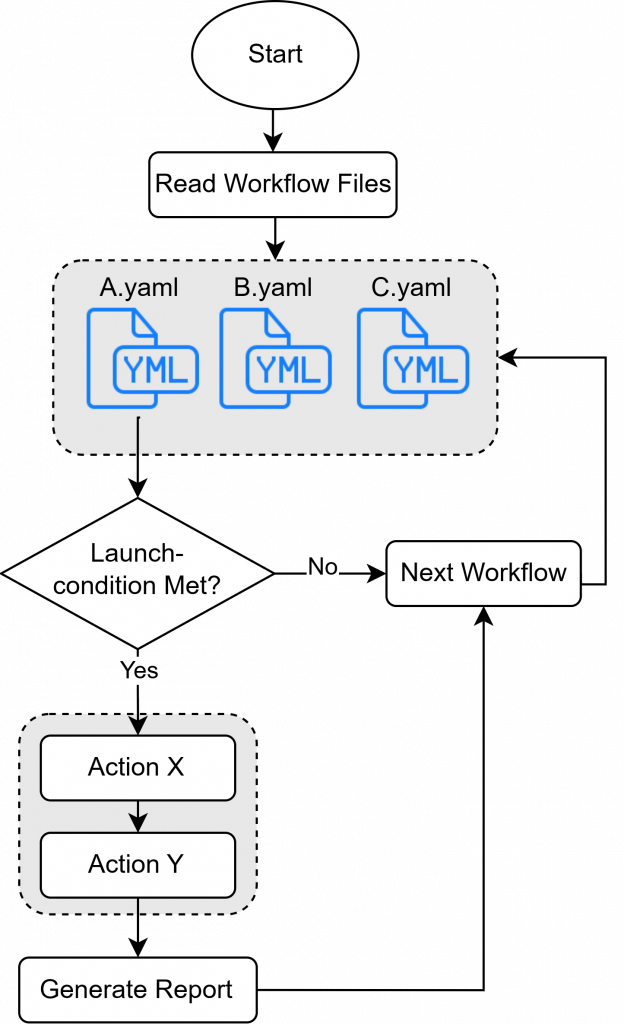
This work provides a valuable basis for supporting IT security teams, analysts and incident responders. The framework lowers the barrier to automating evidence acquisition through YAML-based workflows and encourages further development within the open source community. The time savings achieved lead to significant economic benefits in the long term as resources are used more efficiently.
properties:
title: "Windows Demo"
description: "This is a demo"
author: "John Doe"
launch_conditions:
os: ["windows"]
arch: ["x86", "x86_64"]
actions:
- name: autorunsc
type: binary
attributes:
path: "autorunsc.exe"
log_to_file: true
- name: pdf_files
type: yara
attributes:
rules_paths: |
${CUSTOM_FILES_DIR}\\yara\\*.yara
files_to_scan: |
${USER_HOME}\\Downloads\\*
store_on_match: true
scan_timeout: 4s
- name: find_executables
type: store
attributes:
case_sensitive: false
patterns: |
${USER_HOME}/Downloads/**/*.exe
size_limit: 10 GB
- name: terminal
type: terminal
attributes:
wait: true
separate_window: true
enable_transcript: true
workflow:
- action: autorunsc
timeout: 20s
parallel: true
- action: pdf_files
- action: find_executables
- action: terminal
reporting:
zip_archive:
enabled: true
encryption:
enabled: true
public_key: "example_public.pem"
algorithm: CHACHA20-POLY1305
compression:
enabled: true
size_limit: 100 MB
metadata:
mac_times: true
checksums: true
paths: trueEfficiency
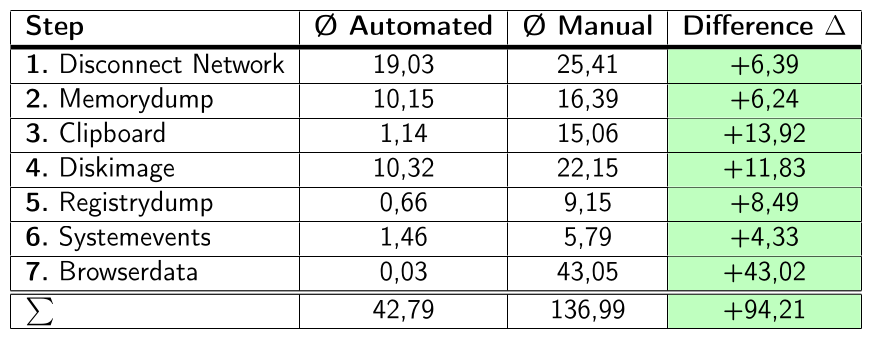
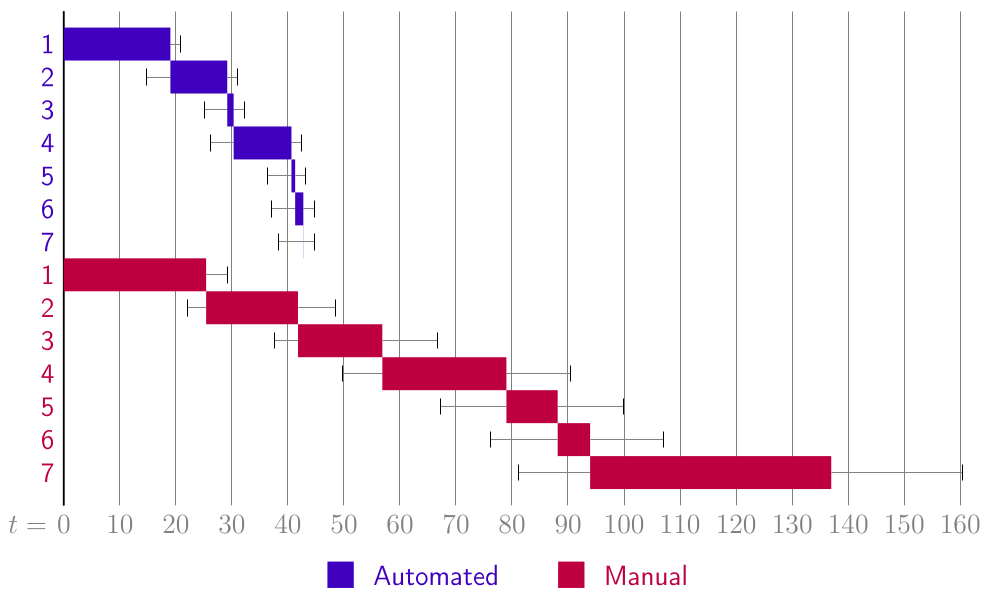
The framework was able to reduce the time required for evidence acquisition by 44% in the worst case and 69% in the best case compared to manual execution. The illustrations show the measurements of a scenario from my bachelor thesis. A total of three scenarios were performed.
Give it a try
Check out the documentation for more instructions on how to get started.
- Fran Casino et al. „Research Trends, Challenges, and Emerging Topics in Digital Forensics: A Review of Reviews“. In: IEEE Access 10 (2022), S. 25464–25493. doi: 10.1109/ACCESS.2022.3154059. ↩︎
- https://www.apple.com/de/newsroom/2020/11/apple-unleashes-m1/ ↩︎
- Statista. Chromebook shipment share of total notebook shipments worldwide from 2019 to 2022. Jan. 2022. url: https://www.statista.com/statistics/1117651/chromebook-shipment-share-of-total-notebook-shipments-worldwide (visited 12.09.2024). ↩︎
- Scientific Working Group on Digital Evidence. Best Practices for Chromebook Acquisition and Analysis. Techn. Ber. 22-F-002-1.0. Version 1.0. National Institute of Standards und Technology (NIST), Sep. 2022. url: https://www.nist.gov/document/swgde- 22- f- 002- 10- best- practices-chromebook-acquisition-and-analysis (visited 12.09.2024). ↩︎
- https://cellebrite.com/ ↩︎
- https://www.magnetforensics.com/de/products/magnet-graykey/ ↩︎